For enterprise users, data security is extremely important. Among various data security assurance methods, Xen virtual technology can provide more complete data security solutions for enterprise users due to its high compatibility and ultra-stable characteristics. This article takes mail server data security as an example, discusses the Xen architecture features and high-performance advantages, and proposes targeted solutions.
The importance of data
Data is the most important thing, everything that is a computer. If there is no data, the computer will have no value in existence. The data is mainly divided into two aspects-storage data and application data. The so-called stored data includes stored materials, documents, program codes, etc .; and application data includes various running programs, such as web servers, mail servers, etc. The scope of this article is mainly for application data, because application data must be timely and timely, which is related to the company's direct interests and operating status. If the company cannot run according to the daily process because of the server downtime, it will be a very bad thing. Among them, the direct and direct loss is economic loss, and the indirect and most important loss is credit and image loss. The reduction of the credit and image of the customer leads to no signing and deeper cooperation. The loss of credit and image to the employees is manifested by the employee ’s loss of information to the company, which leads to inefficiency in the work. Employee conflicts may even cause the company to disintegrate. Therefore, the importance of data is self-evident.
The main factors causing data corruption and loss
From the value of data, we can see that data is directly related to money. It can be said that losing data means losing money, but losing money is uncontrollable, and losing data is controllable. Therefore, our best way is to protect and backup the data, so that even if the data is lost or damaged, you can sit back and relax. Data loss and damage are mainly due to the following two factors:
Soft operation aspects, such as Trojans, viruses, accidental deletion, etc .;
In terms of hardware, such as hard disk damage, array damage, server damage, etc. caused by sudden power outages, especially the damage of the server can directly lead to immediate interruption of daily work.
Fundamental protection against threats to data security
Since the harm to data mainly comes from software and hardware, the protection of data also starts from these two aspects. Let ’s first look at the software. We all know that there is no airtight wall, that is, there is no absolutely secure network, so just installing firewalls and antivirus software for software and hardware cannot completely solve the problem; and hardware damage is also unpredictable and uncontrollable. Yes, so we have to do hot standby. The so-called hot standby is to prepare at least two pieces of hardware, the main and standby, to handle the same business and are both activated, for example, the main server and the standby server are the company's mail server, so that when the main server goes down, the backup server will take over And start working without interrupting the company's mail service. Therefore, the fundamental solution to network security lies in data backup and migration.
General solution for backup and transfer
For data backup and migration, the general approach is as follows:
Hot standby of at least two or more servers
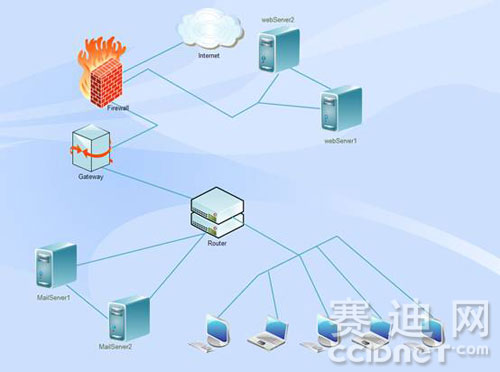
Burn to disc and transfer to network storage, as shown below
Xen's basic principles and ideas
The above figure is a traditional example of traditional backup and migration: when webserver1 and mailserver1 are down, webserver2 and mailserver2 will be started to ensure smooth network and data. But this example is obviously to invest a lot of money to buy new hardware as a backup server, but compared to hardware, software backup and synchronization is safer and easier, and the maintenance capital in the later period is also lower.
Xen is an open source and excellent virtual machine software developed by the University of Cambridge. It has been widely supported by major manufacturers in the industry. It has been integrated into some open source operating systems such as BSD, Solaris, Linux, etc., with the fastest speed and security. It is best to become the most excellent basic virtualization solution. Xen supports multiple operating systems as clients, including Windows, Linux, Solaris, and multiple versions of the BSD operating system, and these operating systems can be installed on the same server or multiple servers. The basic principle of Xen is: Xen virtualization technology implements a lightweight software layer called Xen Hypervisor between server hardware and operating system. In this software layer, the virtual machine or VM is called Domain0, and the client is called DomainU. Domain0 is a virtual machine with special permissions, which provides system management and control services as an extension of the virtual machine. It will be completely separated from the control mechanism, and it will also improve the efficiency of design and development. The operating mechanism of Xen can be seen more clearly from the figure below.
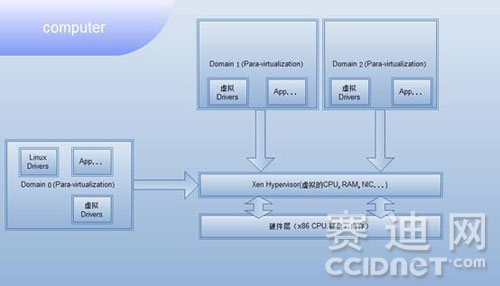
Xen supports Intel VT technology and AMD Pacifica technology, so that it can run an unmodified operating system, it also supports 32 / 64-bit PAE virtual machines, and provides functions such as saving, restoring virtual machines and live migration. Saving and restoring virtual machines can provide users with machine-level protection, so users do not need to care about whether the program itself has a backup function, and then achieve recovery in the event of a server disaster. Such migration and backup can also be performed between different physical computers, and maintenance and upgrades can be performed online.
The following are two common methods for implementing Xen's DomainU virtual machine
Storage Restore Migration Method
The operation process is as follows. First, the current operating state of a DomainU is saved in a file on the hard disk, and then Xen uses this file to restore the original state of DomainU. Just like the hibernation function of a notebook computer, the computer's state is saved as an image stored in the hard disk, and the disk image is restored to the runtime state when it exits from hibernation. Xen backup files can be backed up on the local physical machine, and this file can also be copied to other Xen virtual machines for recovery and operation, just like carrying a computer with you. Subsequently, we can use the network or the set trigger conditions to automatically transfer the backup DomainU file to achieve a faster and more convenient backup.
Dynamic migration
If you have stricter non-stop business requirements or want to minimize downtime, then the benefits of the never-downtime technology provided by Xen are self-explanatory. The specific implementation details are explained below. The current Gigabit network can fully meet the network requirements. As shown in the following figure, first establish an NFS server, establish a DomainU disk file on NFS, establish configuration files on HostB and HostC and perform related configuration and trigger conditions Monitoring etc.
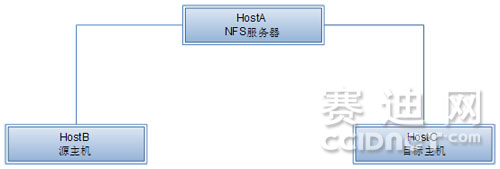
When there is a problem with the HostB server, it will trigger the HostC server to start the same DomainU configuration file, so that after opening, it is the DomainU just now. Xen's mechanism provides an abstraction layer for running multiple virtual hosts on each host, effectively separating the operating system and its applications from the underlying physical host, thereby achieving uninterrupted service and rapid transfer, and Improve server utilization, consolidate host groups, reduce complexity and operation and maintenance costs, and lower the total cost of ownership.
To sum up, Rising analysis believes that Xen is safe, fast, cost-saving and other characteristics, and is an open source project that is developing at a high speed and has unlimited prospects, providing a more Good choice.
The Packaging Sponge is made from PU with soft touch and good handfeeling. It is useful to protect the items from damaging. High quality materials, environmental-friendly and non-toxic. No stimulation to the skin. It is also very absorbent, durable and easy for grip. We are sure we can offer the most competitive prices with good quality to you. Sincrely hope we can cooperate with you.

Packaging Sponge
Packaging Sponge,Protective Foam Sponge,Packing Foam Sponge,Exfoliating Packing Sponge
FengRun Commodity Co.,Ltd. , https://www.sponges.nl